
Base-64 Encoded PE Executable Files
A fairly common method for attackers to sneak an executable past a security control is using base-64 encoding to obscure the bytes of the file. Base-64 converts the bytes of a file into printable ASCII characters making it perfect to use for posting executable files on a text bases website. PE files can be recognized by the header “MZ” or “0x4d 0x5a 0x90”. When they are encoded in base-64 the header will start with “TV”. Below is the Yara rule that I use to find base-64 PE files on Pastebin. For quite a while this technique worked very well to host malware, however PasteBin has taken steps to reduce the amount of malware hosted on their site and now this technique isn’t quite as common.
rule PE_Executable_B64
{
meta:
author = "Jon Lein"
date = "10/23/2020"
description = "PE executable file encoded with Base64."
strings:
$header = /TV(oA|pB|pQ|qA|qQ|ro)\w+/
condition:
$header
}
After finding and downloading a file, I can decode it and run it as a regular executable. Below is the Python program I have written to decode and save them.
import base64
import sys
# make sure only argument is the path to the encoded file
if len(sys.argv) != 2:
print("[!] Usage: Decode_b64-PE.py <path to B64 PE>")
exit()
encoded_file = sys.argv[1]
f = open(encoded_file, "rb")
# keep name of file but remove extension
pe_name = encoded_file.split('.txt')[0]
# remove any spaces in the file name
pe_name = pe_name.replace(' ', '_')
# add executable extension
pe_name += '.exe'
# open file to write executable in
pe = open(pe_name, 'wb')
pe.write(base64.b64decode(f.read()))
pe.close()
f.close()
Non-malicious Use Cases
I have found that just because a PE file is encoded and placed on Pastebin like this, doesn’t mean it’s malicious. There is a wide variety of use cases I have found that don’t push any malware at all.
After extracting the executable and loading it into IDA, I only had to look at the strings to have a good idea that it wasn’t malware but a hack for a video game.
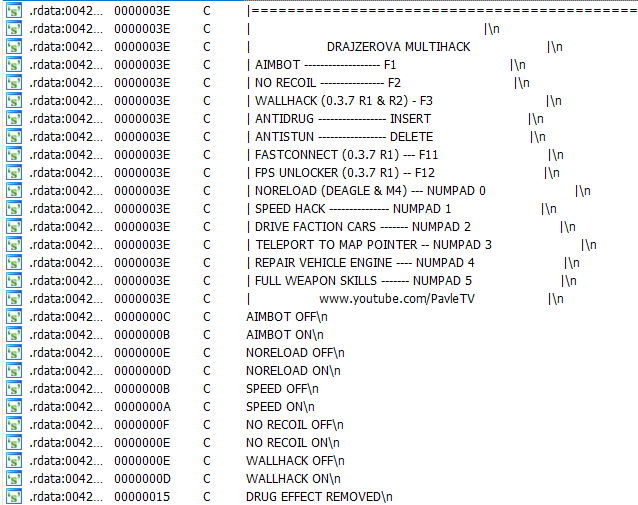
Looking back at the function that was using all of these strings I found the main functionality of the hack. It starts by running a loop until it finds a window called “GTA:SA:MP” referring to Grand Theft Auto: San Andres Multi-Player.
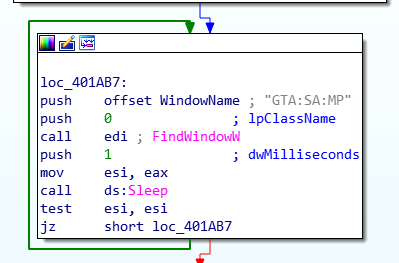
Next it prints the options to the user as found in the strings section. Finally, it is able to use Writeprocessmemory to change attributes of the game.
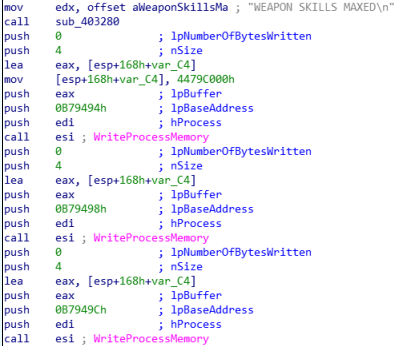
While this strictly isn’t malware, there might be some restrictions to posting this code anywhere due to the game’s terms of service and this could be a way to distribute the code without take-down notices.
Another file I recovered and decoded recently contained the icon for a windows installer after converting it to an exe file. Running it I found a setup wizard for the software GridMove, a legitimate piece of software. I don’t know exactly why this is here, but my guess is that is was an administrator needing to install this software across multiple desktops and was restricted from copying the installer across to all the computers. A script could pull this off of Pastebin and decode it for an end user to install. I have found many different pieces of software and even Windows updates distributed this way. It seems weird to me but there must be some use case that makes this method practical.
Conclusion
Attackers can use Base-64 encoding to deliver executable files over PasteBin. These files are easy to by their “TV” signature. While malware is the main use case for this technique, I have found legitimate uses for it. In the future I will continue to process and write about the ~75% of Base-64 files I have that are parts of malware campaigns.